Hashing
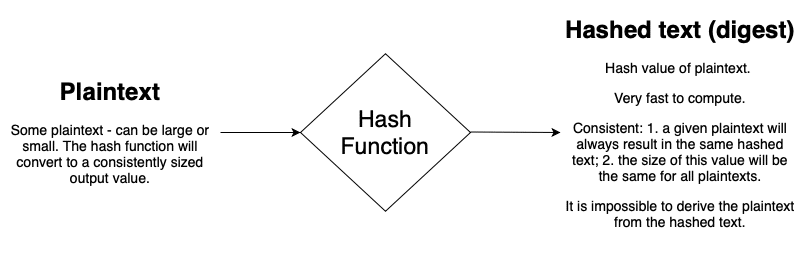
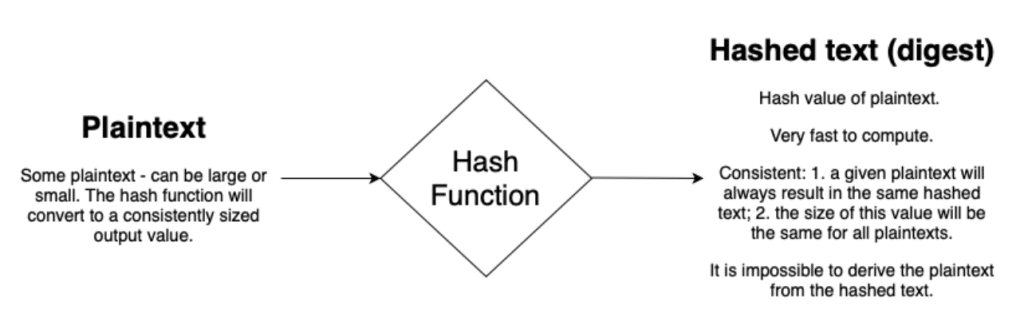
This article will continue our series on cryptography. Our articles to date have discussed random numbers, pseudorandom numbers and cryptographically secure pseudorandom numbers. In this article, we will learn more about hashing, which is the conversion of an input (plaintext) to an output (hashed text or digest), where:
- The input cannot be determined from the output
- The input always yields the same output
- All inputs yield the same length (though different valued) output
Applications
The most familiar application of hashing is for password management. Users have a plaintext password for your system. However, you do not store their plaintext password in your database. Instead, you hash their plaintext password and store the hashed text in your database. Whenever your application authenticates the user, they enter the plaintext into your login form, your server hashes the plaintext and validates the hashed value against the hashed text you have in your DB.
Well-known algorithms
Two of the most well-known hashing algorithms are MD5, SHA, RIPEMD (used by Bitcoin and other cryptocurrencies based on Bitcoin), Whirlpool.
MD5
The MD5 algorithm was designed in 1991, it produces a 128 bit hashed text. It was determined to be insecure for cryptographic purposes as early as 1996 but, despite its shortcomings, is still widely used. One major vulnerability is related to the small size of the hash value (128 bits). With modern computers, brute force attempts to find a collision take seconds. A collision occurs when two plaintext values lead to the same hash value. Finding a collision will not reveal the plaintext but, if you think of the password case above, it would allow you to login as a given user by leveraging the second plaintext that collided with the actual password plaintext.
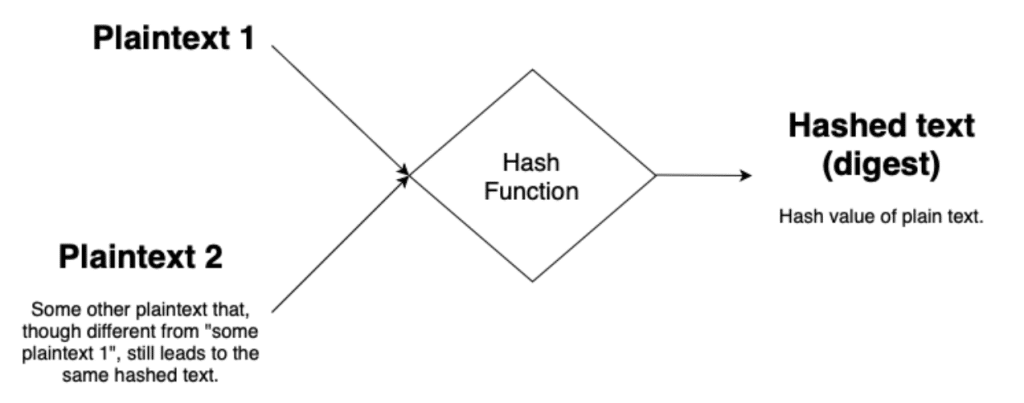
To see examples of MD5 in use, check out this online calculator or see below:
- “Plaintext 1”
- c2c74fd300bd016b3196dd766fba341e
- “Plaintext 2”
- 487ce2f70662d4a32d4bb77012a58e34
SHA
The SHA family of algorithms includes SHA-0 (160 bit), SHA-1 (160 bit), SHA-2 (256 bit or 512 bit) and SHA-3. These were designed by the National Security Agency (NSA) and are published by the National Institute of Standards and Technologies (NIST).
SHA-0 was published in 1993 but was found to be flawed so was replaced by SHA-1. As of 2010, SHA-1 is not recommended, due to vulnerabilities, for cryptographic applications.
SHA-2 consists of 2 algorithms with different digest sizes – the first one produces hashed text 256 bits in length while the second produces hashed text 512 bits in length.
SHA-3 is a new algorithm chosen in 2012 after a competition among designers not affiliated with the NSA. It supports the same hash lengths as SHA-2: 256 and 512 bits.
To see examples of SHA in use, check out this online calculator or see below:
- SHA-1 160 bit “Plaintext 1”
- de8cf334b640b8c0f453d0b3d0d70a6a8db832cd
- SHA-2 256 bit “Plaintext 1”
- 45c13373874330f60b817f5c29e99d8beda3990e2c343f89a2575384eccf7d43
- SHA-2 512 bit “Plaintext 1”
- 37fe15092c1bab37f0405f2f8306c495db1288640215146c1e99ebddc9b1f7bd0ea70206fd2825967e80475eefd9f6a081e7fe0c39528d77d9d8fa2f8436c6e6
- SHA3-256 bit “Plaintext 1”
- c53960ef37e7e2f40b47c7d6fb967291eb8f47a7b01bb7e409504df255d6f453
- SHA3-512 bit “Plaintext 1”
- 7be341d1848e324a210e9b710ed616a908b807bf6022cf387d603be36b2b9e3c6230ec4d67e696f843addc82242c9458d29e4df98191634d60290fd5e469c999
Next up
Next we will discuss digital signatures.
