Digital signature
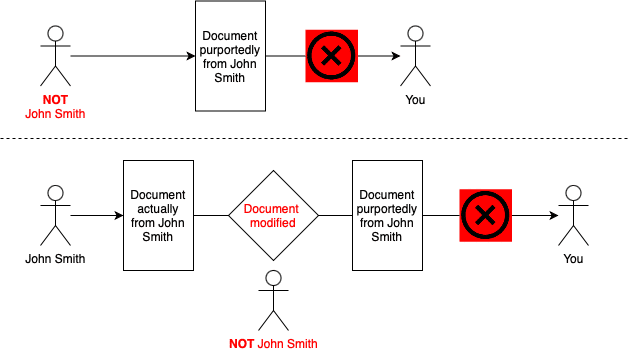
This article will continue our series on cryptography. Our articles to date have discussed random numbers, pseudorandom numbers, cryptographically secure pseudorandom numbers and hashing. In this article, we will learn more about a digital signature, which is the electronic equivalent of a handwritten signature. Digital signatures guarantee that a document is from a given sender and that it has not been altered. Without a digital signature, if you receive a document electronically from John Smith, there is no way to be sure that John Smith actually sent you the document or, assuming that John Smith actually sent you a document, that the document you received was identical to the version John sent.
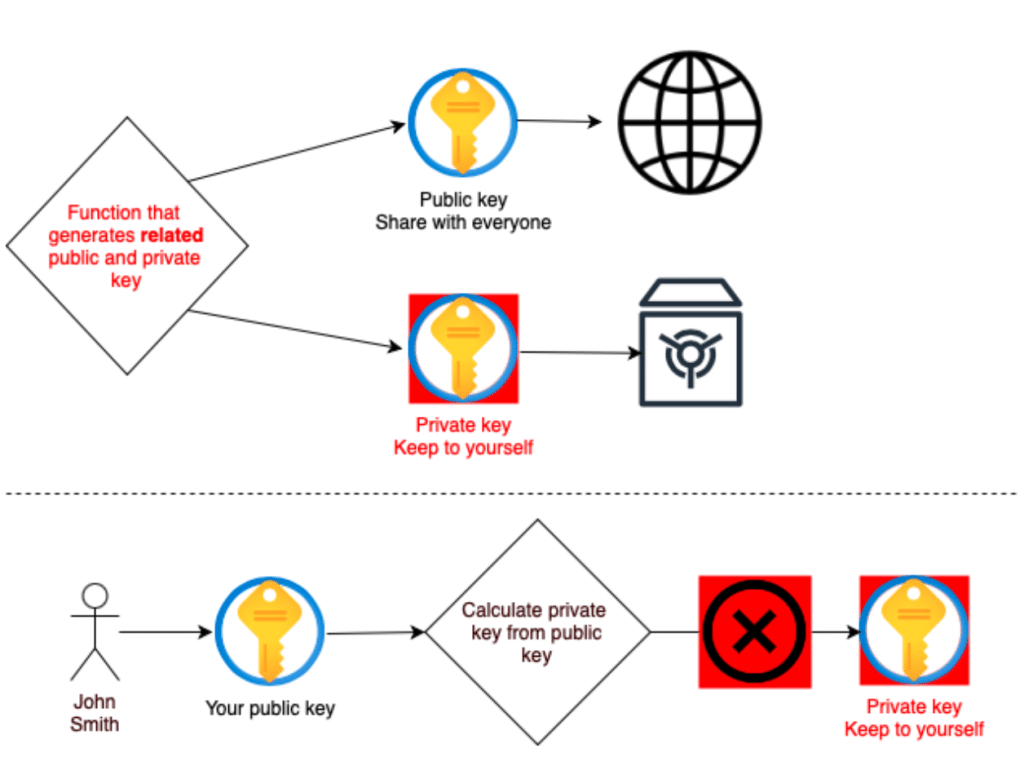
Public key cryptography
Digital signatures are based upon public key cryptography – cryptography whereby a related pair of keys, public and private, are generated. These key pairs are generated mathematically by one-way functions, much like the hash functions we discussed last week. One-way functions are efficient to calculate in one direction but practically impossible to reverse. For our key pair, if someone has your public key, there is no way for them to determine the related private key. Due to this mathematical property, you share your public key with everyone through public key infrastructure (PKI).
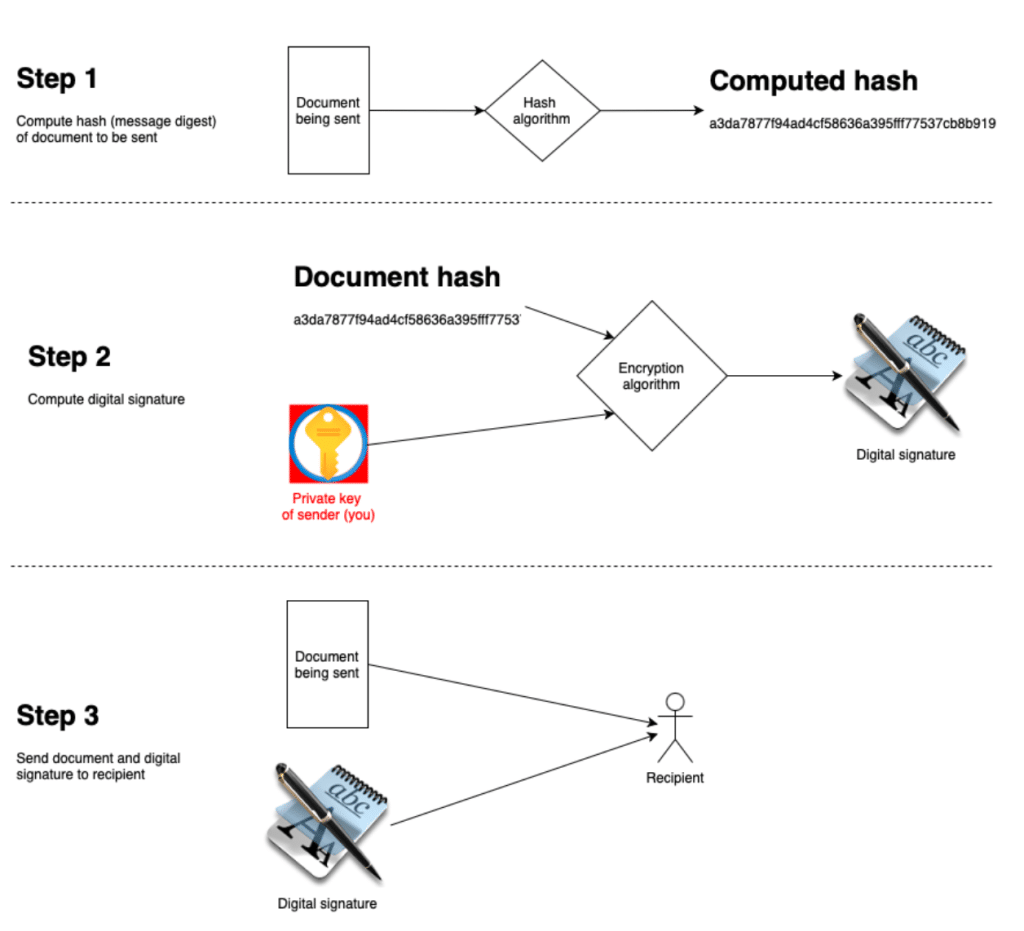
Signing process
For digital signatures, the signing process computes the signature using 2 inputs: the document itself and your private key. You then send the document and the digital signature to the desired recipient. The recipient validates that the document is from you and is unaltered using your public key, which everyone has access to. The sending process is as follows:
- Compute the hash (message digest) of the document
- Encrypt the document’s hash using the sender’s private key
- This is the digital signature
- Send the document & digital signature to the recipient
Validation process
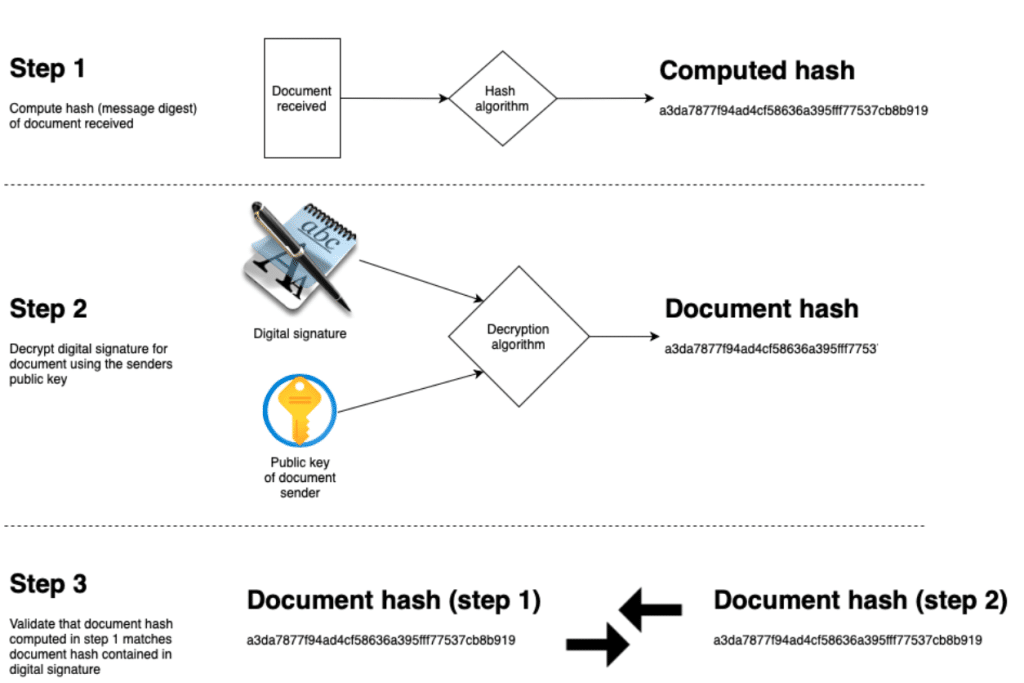
The receiving / validation process is as follows:
- Compute the hash (message digest) of the document
- Decrypt the digital signature using the sender’s public key
- This is the documents hash (message digest)
- Verify that 1 = 2a
Next up
We will discuss https.
