Digital certificates
This article will continue our series on cryptography. Our articles to date have discussed random numbers, pseudorandom numbers, cryptographically secure pseudorandom numbers hashing and digital signatures. In this article, we will learn more about digital certificates. Digital certificates are used to validate the identity of companies, websites, email addresses or even individuals. Digital certificates are obtained from certificate authorities, which are companies, who are trusted third parties, that verify the identity of entities, then issue and store certificates.
Examples of certificate authorities are: Let’s Encrypt; Comodo; Digicert.
How certificate authorities create digital certificates
As an example, say you wish to obtain a digital certificate for your website abc.com.
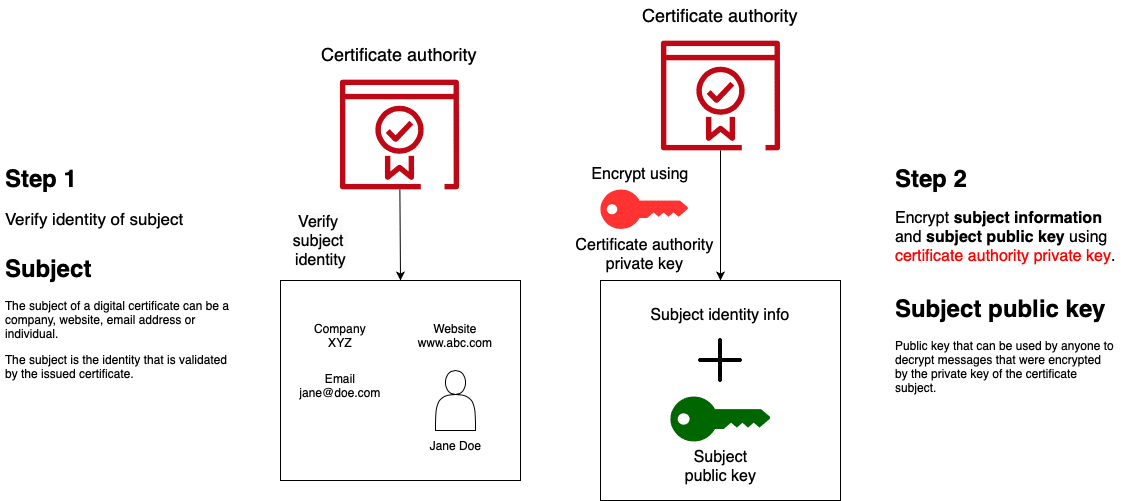
You provide the certificate authority with information about you, as owner of the abc.com domain. You also provide them with a public key, which is paired by a private key which you keep to yourself.
The certificate authority will verify that you are, in fact, the owner of the abc.com domain and will issue you a certificate. This is effectively them, as a trusted third party, vouching for your identity in a digital way. To create the digital certificate they will digitally sign, using their private key, your identifying information and public key.
You then configure your website to use this certificate and to have access to the private key, which is the pair of the public key included in your certificate.
We will discuss https in more detail in the next post but, now that your site has its digital certificate, you can accomplish end to end encryption between your website and its users.
Next up
Next we will discuss https.
